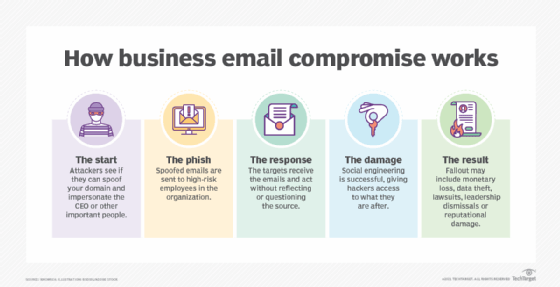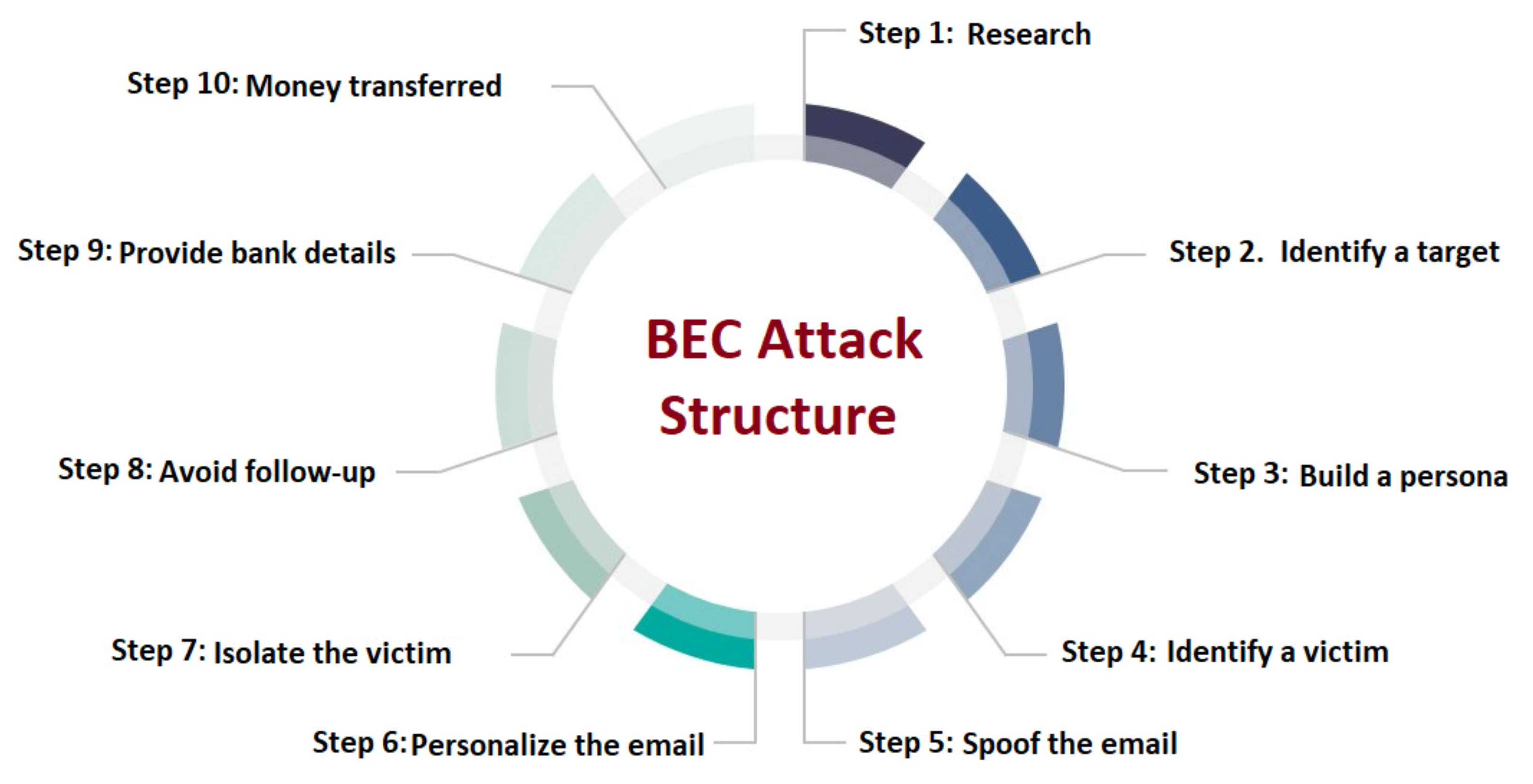
Electronics | Free Full-Text | Business Email Compromise Phishing Detection Based on Machine Learning: A Systematic Literature Review

Armorblox Email Security Threat Report Reveals 72% Rise in Business Email Compromise Attacks in 2022

Behind the scenes of business email compromise: Using cross-domain threat data to disrupt a large BEC campaign | Microsoft Security Blog
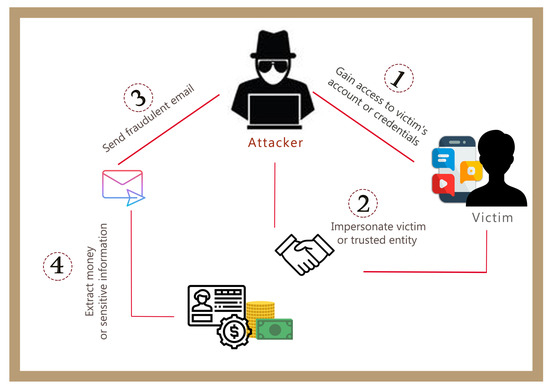
JCP | Free Full-Text | Business Email Compromise (BEC) Attacks: Threats, Vulnerabilities and Countermeasures—A Perspective on the Greek Landscape




.png)